Exploiting an Exposed Swagger File to Achieve RCE
بِسْمِ اللَّـهِ الرَّحْمَـٰنِ الرَّحِيم
Hello there, here is Mohamed Elhadad, a cyber security Engineer at Isec.
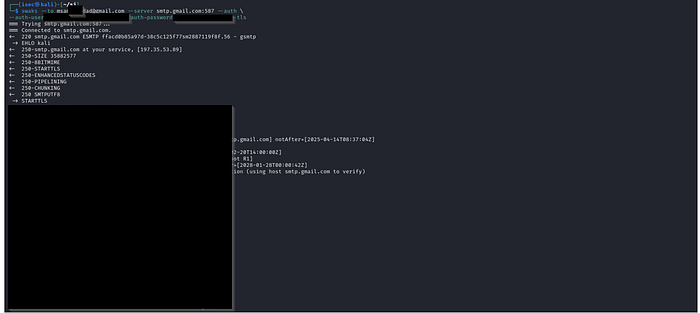
During a recent black-box penetration test, we discovered a publicly exposed Swagger file. This led us down a path of exploitation, uncovering multiple critical vulnerabilities, including broken access control, local file disclosure, sensitive information exposure, and ultimately, remote code execution (RCE).

Key Points
- Exposed Swagger File: Provided detailed API documentation, facilitating reconnaissance.
- Broken Access Control: Allowed unauthorized access to sensitive endpoints.
- Local File Disclosure: Accessed
appsettings.jsonvia thepathparameter. - Sensitive Information Exposure: Found JWT secrets, MSSQL, and Hangfire credentials.
- Administrative Access: Used Hangfire credentials to log in as an admin
- Remote Code Execution: Enabled
xp_cmdshellin MSSQL to achieve RCE.

1. Finding the Exposed Swagger File
While performing enumeration, we stumbled upon an exposed Swagger endpoint (/swagger/v1/swagger.json). This file provided us with detailed API documentation, including endpoints, parameters, and expected responses. Such exposure can significantly ease an attacker's reconnaissance process.

2. Exploiting Broken Access Control
Through the endpoints listed in the Swagger documentation, we tested for authorization flaws. We identified several endpoints vulnerable to broken access control, one of which was:
GET /api/attachments/download?path=We realized that this endpoint lacked proper authorization checks, allowing us to manipulate the path parameter and access arbitrary files on the server.
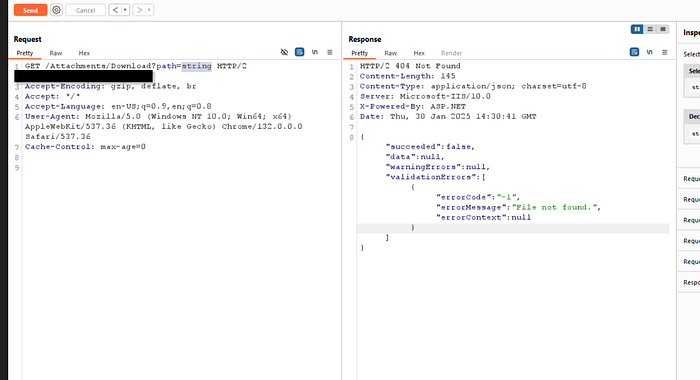
As shown in the previous screenshot, we were able to access this endpoint.
3. Local Fie Disclosure (LFD) Attack
Using the vulnerable endpoint, we attempted to read sensitive files on the server. Our first target was the web.config file:
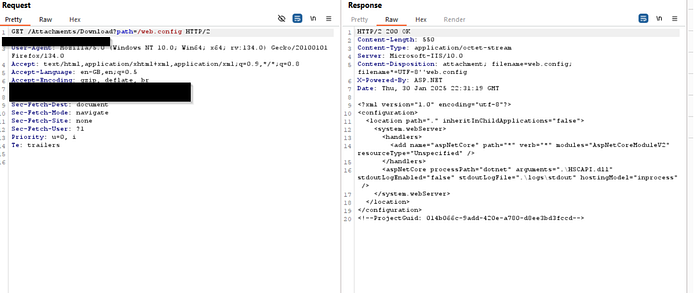
However, since the application was built on .NET Core, the web.config file did not contain sensitive information. We shifted our focus to the appsettings.json file, commonly used in .NET Core applications for configuration settings:


This attempt was successful, and the appsettings.json file revealed several juicy credentials:
- JWT Secret: Used for signing and verifying authentication tokens.
- MSSQL Credentials: Database username and password.
- Hangfire Credentials: Username and password for the Hangfire dashboard.
4. Abusing Hangfire Dashboard Access
With the Hangfire credentials extracted from the appsettings.json file, we were able to log in to the Hangfire dashboard. This gave us administrative access to the task management interface, allowing us to execute jobs on the application server.

5. MSSQL Access and Enabling xp_cmdshell
Next, we connected to the MSSQL server using the credentials found in the configuration file. Our goal was to achieve remote code execution (RCE) by enabling the xp_cmdshell feature:

Enabling xp_cmdshell allowed us to execute system commands directly from the MSSQL server, achieving full remote code execution on the target machine.

6.Website Access Using Extracted Credentials
We were able to log in to the website using the credentials found in the appsettings.json file, as shown in the screenshot below.

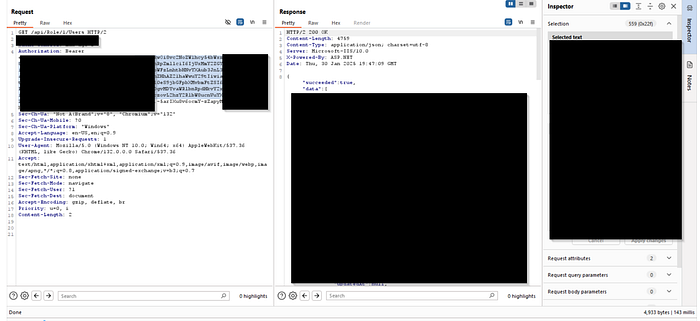
7. Privileged Endpoint Access Using JWT Secret Key
Using the extracted JWT secret key, we were able to generate tokens and access any endpoint with elevated roles, as shown in the screenshot below.

8. Email Sending Capability
As shown in the screenshot below, we were able to send emails through the application.